Better Dev Link
Feed since 23 Mar 2019BetterDev.Link collects links around the web that aims to help you learn something new. The topics aren't tight to any specific programming languages, technologies or frameworks but attempt to include resources that might help you learn a thing or two from them. See: https://betterdev.link/
To subscribe to and get updates from Better Dev Link in your feed stream, sign up, or see the rest of our feeds.
GitHub - joanrod/star-vector: StarVector is a foundation model for SVG generation that transforms vectorization into a code generation task. Using a vision-language modeling architecture, StarVecto...
star-vector a foundation model for SVG generation that transforms vectorization into a code generation task. Using...

goavatar
goavatar This package provides a simple way to generate unique, symmetric identicons based on an input...
GitHub - lakekeeper/lakekeeper: Lakekeeper is an Apache-Licensed, secure, fast and easy to use Apache Iceberg REST Catalog written in Rust.
lakekeeper an Apache-Licensed, secure, fast and easy to use Apache Iceberg REST Catalog written in Rust....
GitHub - gopasspw/gopass: The slightly more awesome standard unix password manager for teams
gopass The slightly more awesome standard unix password manager for teams

30 years of PostgreSQL buffer manager locking design evolution
30 years of PostgreSQL buffer manager locking design evolution An in-depth exploration of the evolution of...

How to Write Blog Posts that Developers Read
How to Write Blog Posts that Developers Read A guide offering practical advice on crafting technical...

Identity Tokens Explained: Best Practices for Better Access Control
Identity Tokens Explained: Best Practices for Better Access Control An overview of identity tokens, detailing their...

Blasting Past Webp
Blasting Past Webp: An analysis of the NSO BLASTPASS iMessage exploit A technical analysis by Google’s...
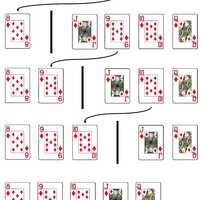
Visual-Focused Algorithms Cheat Sheet
Visual-Focused Algorithms Cheat Sheet A concise reference guide summarizing key algorithms related to visual data processing,...

Train & Weather Tracker with Raspberry Pi & E-Ink
Train & Weather Tracker with Raspberry Pi & E-Ink If you have some old Raspberry Pi...
MySQL transactions per second vs fsyncs per second
MySQL transactions per second vs fsyncs per second An examination of the relationship between MySQL’s transaction...
Laurence Tratt: Better Shell History Search
Better Shell History Search An article discussing techniques to enhance shell history search functionality, including the...
Life Altering Postgresql Patterns
Life Altering PostgreSQL Patterns A discussion on transformative PostgreSQL design patterns, such as using UUID primary...
A Practical Guide to Taming Postgres Isolation Anomalies
A Practical Guide to Taming Postgres Isolation Anomalies A comprehensive guide addressing PostgreSQL’s transaction isolation anomalies,...
Open-sourcing OpenPubkey SSH (OPKSSH): integrating single sign-on with SSH
Cloudflare open-sourcing OpenPubkey SSH (OPKSSH): integrating single sign-on with SSH Single sign-on for SSH is a...
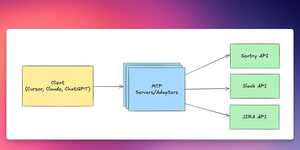
MCP (Model Context Protocol): Simply explained in 5 minutes
MCP (Model Context Protocol): Simply explained in 5 minutes An introduction to the Model Context Protocol...
GitHub - habedi/hann: A fast approximate nearest neighbor search library for Go
hann A fast approximate nearest neighbor search library for Go
GitHub - Kither12/shezem-rs: Audio recognition CLI
shezem-rs A Rust implementation of a fast audio fingerprinting system inspired by Shazam, for audio recognition...
GitHub - pgr0ss/pgledger: A ledger implementation in PostgreSQL
pgledger A ledger implementation in PostgreSQL
GitHub - amd/gaia: Run LLM Agents on Ryzen AI PCs in Minutes
gaia A tool by AMD to run LLM Agents on Ryzen AI PCs in Minutes
GitHub - Stability-AI/stable-virtual-camera: Stable Virtual Camera: Generative View Synthesis with Diffusion Models
stable-virtual-camera Generative View Synthesis with Diffusion Models
GitHub - xataio/agent: AI agent expert in PostgreSQL
xata agent an open source agent that monitors your database, finds root causes of issues, and...
GitHub - ariga/atlas: Manage your database schema as code
atlas A database schema management tool that works like Terraform—diff, apply, and keep your schema in...

typespec.io
typespec Define your API once in a simple tsp file, then generate OpenAPI, gRPC, client code,...

Ferron - a fast, memory-safe web server written in Rust
ferronweb A fast, memory-safe web server powered by Rust. Similar to Caddy or Nginx but written...
pgFormatter
pgFormatter Free Online version of pgFormatter a PostgreSQL SQL syntax beautifier (no line limit here up...
When you deleted /lib on Linux while still connected via ssh
When You Deleted /lib on Linux While Still Connected via SSH A classic tale of Linux...

A SQL MERGE statement performs actions based on a RIGHT JOIN
Think About SQL MERGE in Terms of a RIGHT JOIN RIGHT JOIN is an esoteric feature...

Zero-knowledge proofs
Zero-Knowledge Proofs An approachable introduction to the magic of zero-knowledge proofs—how they let you prove something...
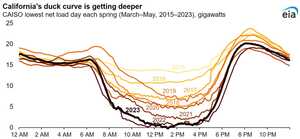
Understanding Solar Energy
Understanding Solar Energy This one’s a bit outside the usual programming realm, but trust me—it’s fascinating....
Green Vitriol - A synchronization engine for everyone
A Synchronization Engine for Everyone Syncing data is one of those things that sounds easy until...

Leaking Passwords (and more!) on macOS | Watch This Space
Leaking Passwords (and more!) on macOS A deep dive into how macOS can unintentionally leak sensitive...

A Deep Dive into the Inline Background Overlap Problem – Frontend Masters Blog
A Deep Dive into the Inline Background Overlap Problem Ever tried putting text over an image...
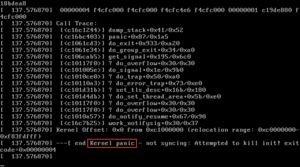
BPF or How I Learned to Stop Worrying and Love the Kernel
BPF: Or How I Stopped Worrying and Loved the Kernel BPF is like a superpower for...
A History of Null Pointer Dereferences on macOS
A History of Null Pointer Dereferences on macOS A nostalgic yet technical look at how null...
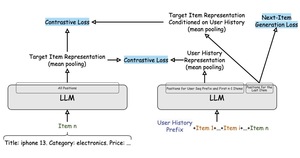
Improving Recommendation Systems & Search in the Age of LLMs
Improving Recommendation Systems & Search in the Age of LLMs AI-powered recommendations are everywhere, but how...
Intro - Ruby, Ractors, and Lock-Free Data Structures
Ruby Ractors and Lock-Free Data Structures If you’re a Rubyist curious about parallelism, this is for...
GitHub - smparsons/retroboy: A Game Boy emulator written in Rust.
retroboy A Game Boy emulator written in Rust.
GitHub - ksylvest/rhino: A Rack web server written in Ruby from scratch.
rhino A Rack web server written in Ruby from scratch.

GitHub - konvajs/konva: Konva.js is an HTML5 Canvas JavaScript framework that extends the 2d context by enabling canvas interactivity for desktop and mobile applications.
konva an HTML5 Canvas JavaScript framework that extends the 2d context by enabling canvas interactivity for...

GitHub - Zouuup/landrun: Run any Linux process in a secure, unprivileged sandbox using Landlock. Think firejail, but lightweight, user-friendly, and baked into the kernel.
landrun Need to run untrusted code safely? This sandboxing tool might be your new best friend.

GitHub - rudransh61/Physix-go: A simple Physics engine in GoLang
Physix-go A physics engine in Go that makes simulating motion, collisions, and forces as simple as...

GitHub - fastplotlib/fastplotlib: Next-gen fast plotting library running on WGPU using the pygfx rendering engine
fastplotlib A blazing-fast plotting library for massive datasets, using modern GPU rendering to keep things smooth.
GitHub - EzequielRamis/zimdjson: Parsing gigabytes of JSON per second. Zig port of simdjson with fundamental features.
zimdjson Parsing gigabytes of JSON per second. Zig port of simdjson with fundamental features.
GitHub - microsoft/playwright-mcp: Playwright Tools for MCP
playwright-mcp A Model Context Protocol (MCP) server that provides browser automation capabilities using Playwright. This server...
GitHub - julienbourdeau/debugbar: Powerful devtools for Ruby on Rails. Inspired by the Laravel Debugbar.
debugbar Powerful devtools for Ruby on Rails. Inspired by the Laravel Debugbar.

GitHub - crmne/ruby_llm: A delightful Ruby way to work with AI. No configuration madness, no complex callbacks, no handler hell – just beautiful, expressive Ruby code.
ruby_llm A delightful Ruby way to work with AI. No configuration madness, no complex callbacks, no...
GitHub - pipecat-ai/smart-turn
smart-turn an open source, community-driven, native audio turn detection model. Hugging Face model is available
GitHub - addyosmani/filter: Filter - Web Image Editor
filter a powerful, web-based image editor built with React and TypeScript. It provides a modern, intuitive...