The answer is 42! Fedora Linux 42, that is. - Fedora Magazine
Seventy-five thousand generations ago, our ancestors set a vast computer in motion, asking it to produce...
Ursa - ClickHouse Research Fork
During the New Year holidays at the end of December 2024, I decided to fork ClickHouse...
Arch Linux now has an official WSL image
…and it is officially (re)distributed by Microsoft! A few months ago, the eventuality of building and...
AerynOS
This is Ikey Doherty’s project following Solus and Clear Linux. P.s. any idea why people keep...
Getting Started with W65C832
The W65C832 FPGA Core (by Michael Kohn) is based on the WDC 65C816 ISA, but offers...

What Makes a Great Developer Experience? » Code Simplicity
I’ve been working for over 20 years in the field of “developer experience,” where we help...
Async from scratch 2: Wake me maybe | natkr's ramblings
So. You've read my last post. You got inspired. Excited, even. Deployed SimpleFuture to production. Spun...

Stevens: a hackable AI assistant using a single SQLite table and a handful of cron jobs
There’s a lot of hype these days around patterns for building with AI. Agents, memory, RAG,...

Tidbyt without the company
Remember the Tidbyt? It’s a super low-resolution, internet-connected, wood-paneled display that I wrote a review of...

MacPad: How I Created the Hybrid Mac-iPad Laptop and Tablet That Apple Won’t Make
It all started because I wanted a better keyboard for my Vision Pro. I had no...

An ssh adventure; or, why l10n support is important(*) ($2149340) · Snippets · GitLab
this is IMPECCABLE work i was on the edge of my seat the whole time i...
UW PLSE | Algebraic Semantics for Machine Knitting
As programming languages researchers, we’re entitled to a certain level of mathematical rigor behind the languages...
Python is an interpreted language with a compiler | nicole@web
After I put up a post about a Python gotcha, someone remarked that "there are very...

We don’t need no virtualization
If you think about it, the main use case for virtualization is isolation: Given that you...
</> htmx ~ Documentation
htmx is a library that allows you to access modern browser features directly from HTML, rather...

Global rename and find references
Gleam is a type-safe and scalable language for the Erlang virtual machine and JavaScript runtimes. Today...
sanitizer-fun
Both GCC and Clang support the -fsanitize=undefined flag which instruments the generated code to detect places...

An Ars Technica history of the Internet, part 1
By the end of the 1970s, computers had improved significantly. The invention of the microprocessor set...
What are you doing this week? | Lobsters
What are you doing this week? Feel free to share! Keep in mind it’s OK to...
Ditch the DIY Drama: Why Use Fedify Instead of Building ActivityPub from Scratch?
So, you're captivated by the fediverse—the decentralized social web powered by protocols like ActivityPub. Maybe you're...

Ship Software That Does Nothing - Kerrick Long's Blog
You should ship software that does nothing. Absolutely nothing. I’m not being cheeky about this. I...
Solving One Million Sudoku Puzzles per hour - Recursion
Yesterday night I was bored. I enjoy solving Sudokus by hand and wondered for quite some...

The Five Critical Roles of Your Team
Written by in Long ago, my brother and I shared a room, and we’d stay up...

Speeding up Terraform caching with OverlayFS
The Terraform plugin cache does not support↗ concurrent terraform init runs. This is a massive inefficiency...
DSLogic U3Pro16 Review and Teardown
The year was 2020 and offices all over the world shut down. A house remodel had...

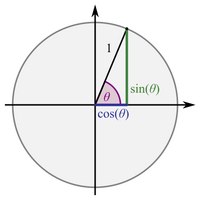
RNG and Cosine in Nix
NixOS is an immutable, atomic Linux distribution with a declarative and reproducible configuration and packaging system...