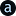~lobsters | Bookmarks (1959)
-
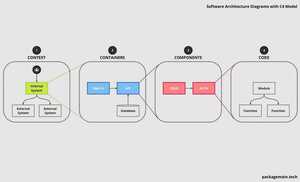
Software Architecture Diagrams with C4 Model
4 Layers of C4 Model: Context, Containers, Components, and CodeRead the original article on packagemain.techA picture...
-
Noel Welsh: Understanding Virtual Machine Dispatch through Duality
For the next edition of Scala with Cats I'm writing a section on implementing interpreters. In...
-
WiFi auth with OsmoHLR/SIM cards
Using WPA-Enterprise with EAP-SIM to authenticate against a network using SIM cardsWireless networks can authenticate clients...
-
An idea on distraction
Suddenly, your inbox is full of messages: John: Do you have 5? You push back from...
-
‘He was in mystic delirium’: was this hermit mathematician a forgotten genius whose ideas could transform AI – or a lonely madman?
Alexander Grothendieck’s mathematical work is by far the most important influence on my own. I’m not...
-
Alex Pliutau | My first experience with Gleam Language
Tue, Aug 27, 2024 5-minute read Over the past few months, I saw a growing amount...
-
Heart of dark mode: done, and still in progress
Earlier this summer, after many passionate requests, Tailscale finally joined the dark side. That is to...
-
SSH CA with device and identity attestation: ssh-tpm-ca-authority
The past year I have been hacking around on tools utilizing TPMs, and one of the...
-
CHERI Myths: I don’t need CHERI if I have safe languages
There’s a recurring myth that CHERI and safe languages are solving the same problems and that,...
-
PQC for non-cryptographers
Yesterday, Chandler asked about an overview of the new PQC algorithms, including hybrids, for non-cryptographers. And...
-
Current zlib-rs performance
Our zlib-rs project implements a drop-in replacement for libz.so, a dynamic library that is widely used...