~hackernoon | Bookmarks (1963)
-
How to Stop Your Scripts from Crashing with Try-Catch Magic
An error in a PowerShell script will prevent it from completing script execution successfully. Using error...
-
Bluesky's Free API Helps Me Curate My Top Posts Like Never Before
Learn how to programmatically fetch and embed your liked Bluesky posts using authentication, API calls, and...
-
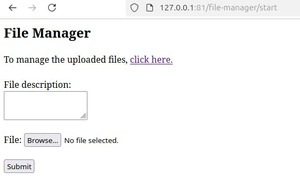
You Don't Need a Lot of Code to Build a Web File Manager
Build useful web application in less than 100 lines of code.
-
Let's Build a Free Web Scraping Tool That Combines Proxies and AI for Data Analysis
Learn how to combine web scraping, proxies, and AI-powered language models to automate data extraction and...
-
New Feature in Go Makes it Easier to Iterate, Manipulate JSON Data
What if you could loop through your JSON data, grab the path of each item, and...
-
Easily Win Arguments By Avoiding These 8 Logic Traps
Some arguments are full of nonsense and logic traps. Learn to spot 8 common fallacies (like...
-
The TechBeat: Lumoz Protocol Mainnet Launch: MOZ Tokens and Node Claims Now Open! (12/17/2024)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
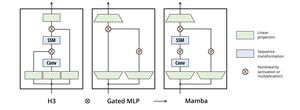
A Simplified State Space Model Architecture
A simplified state space model (SSM) architecture merges linear attention and MLP components into a single,...
-
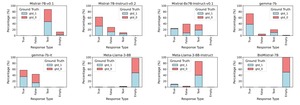
How Extra Information Affects AI’s Ability to Think Logically
LLMs show a nuanced response to increasing distractors: Gemma-7b faces significant accuracy declines, while Mistral-7B Instruct...
-
The HackerNoon Newsletter: Understanding the Twitter API So You Can Design Your Own (12/16/2024)
How are you, hacker? 🪐 What’s happening in tech today, December 16, 2024? The HackerNoon Newsletter...
-
INTMAX Launches First Stateless Layer 2 Payment Solution On Ethereum
INTMAX is the world's first stateless Layer 2 payment solution for Ethereum. The testnet currently operates...
-
Meet dRPC: HackerNoon Company of the Week
HackerNoon's Company of the Week features dRPC, a decentralized Web3 infrastructure provider with focus on resilience...
-
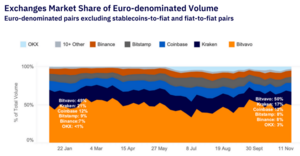
Bitvavo Ranked as the Top EUR spot Exchange by Kaiko, 2024
Amsterdam, December, 2024 – Bitvavo has once again solidified its position as the largest EUR spot...
-
Understanding the Twitter API So You Can Design Your Own
In this article, we explore how the X (Twitter) home timeline (x.com/home) API is designed and what approaches...
-
The One Tool You Absolutely Need to Efficiently Scale Retrieval-Augmented Generation
Achieve efficiency and reliability in your GenAI RAG workflows with KubeMQ for seamless message handling and...
-
Gain More Control Over Your Smart Bulbs With This One Simple Handy Tool
Learn to replace Philips Hue's proprietary automation with Home Assistant's.
-
Never Listen to Alarmist, and Other Career Advice I Would Give Myself If I Could Go Back in Time
Having had a nearly 4-year career, I realize some things that as a student I could...
-
CBDCs Hold Promise and Peril in Global Finance Overhaul, Study Finds
CBDCs can boost financial inclusion, efficiency, and monetary policy but raise concerns about privacy, digital literacy,...
-
New Tool Promises Faster Websites with Streamlined Server-Rendered UI
The [HMPL] project is a small template language for displaying UI from server to client. It...
-
iPhones Could Become More Expensive Under the Trump Presidency
Trump has proposed to place a 60% tariff on imported goods from China, alongside a 25%...
-
Quickly Bulk Load Image to E-commerce Sites With This Guide
Manually updating each image one by one is not only time-consuming but also inefficient. This is...
-
EIP-7503: Zero-knowledge Wormholes for Private Ethereum Transactions
EIP-7503 is a protocol-layer solution for making on-chain transfers on the Ethereum network private. EIP-7503 differs...
-
The TechBeat: Everything You Need to Know About the Lumoz Token Generation Event (12/16/2024)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
Pepeto Introduces Advanced Features For Memecoin Enthusiasts
Pepeto is currently in its presale phase, with tokens priced at $0.000000098 per token. Pepeto distinguishes...