~hackernoon | Bookmarks (2012)
-
Building a Scalable Patent Search Platform for Enhanced IP Management
Maruti Techlabs offers end-to-end product development. Innovate, validate, and launch with our expert team guiding you...
-
Graph Neural Networks for Image Similarity: An Alternative to Hashing?
Traditional hashing techniques like perceptual hashing (pHash) and locality-sensitive hashing (LSH) are widely used for image...
-
Pelagoo’s Project: Solutions for Micro - Mobility and Health on Kalamos Island
In the heart of the Mediterranean, Kalamos Island faces the challenges that often come with remote...
-
Security Expert Says the Bybit Hack May Have Involved an Insider
Dexaran, author of ERC-223 and head of Ethereum Commonwealth, has looked deeper into the attack itself...
-
AI In Content Production: A Friend, Not Foe?
Leo Ovdiienko, COO & Co-founder of Storyby, explores AI’s role in content creation and why production...
-
Can a Powerful AI Model Be Built on a Budget?
Researchers created a new s1 model based on Alibaba’s Qwen2.5 and paid $50 for tokens to...
-
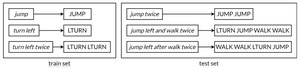
Do Large Language Models Have an Internal Understanding of the World?
Skeptics argue that LLMs, trained on next-token prediction, lack true world models. However, research suggests they...
-
CEO of Crypto Media Outlet Spills The Beans on Establishing Authority in the Crypto Space
Sebastian Scheplitz, CEO of The Coinomist, we will give you an overview of the key aspects...
-
Spynn Publicity's Strategy to Make Apple's iPhone 16e Launch a PR Success
Spynn Publicity, a high-tech PR agency specializing in media campaigns, has outlined a strategy that could...
-
Chatbots Have Been Failing Us for 20 Years—Can AI Finally Fix It?
The first-ever chatbot for customer interactions was created all the way back in the early 2000s....
-
Show Me Your Faith and I will Show You My Work
The future belongs not to those with the most impressive certificates, but to those with the...
-
Can’t Sleep? Maybe Your Brain Just Needs a Distraction—Not a Sedative
Sleep can be described as the interval that sets of electrical and chemical signals have interactions...
-
The HackerNoon Newsletter: Bybit Only Has Itself to Blame (2/25/2025)
How are you, hacker? 🪐 What’s happening in tech today, February 25, 2025? The HackerNoon Newsletter...
-
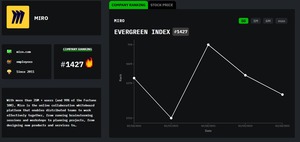
Meet Miro: HackerNoon Company of the Week
Miro's Innovation Workspace - an AI-powered collaboration platform - allows teams to collaborate on projects, prototypes,...
-
How AI Learns Words but Not Meaning
AI models can mimic human language fluently but struggle with true understanding. Critics argue they lack...
-
Do AI Models Challenge the Need for Innate Grammar?
The success of LLMs in learning syntax without innate grammatical knowledge challenges traditional nativist claims about...
-
The AI Compositionality Debate
AI models face a long-standing debate on compositionality. While some claim neural networks must implement symbolic...
-
Building Africa’s Digital Future: Interview with Startups of the Year 2024 Nominee, NAYAMAX
NAYAMAX, a leading African e-commerce SaaS startup, is nominated for HackerNoon’s Startups of The Year 2024...
-
Trash and auto purge from Gmail. How to leverage Apps Scripts to make your life easier!
An abusive partner is sending atrocious emails, the counterpart trashes them but, in moments of weakness,...
-
Facilitating a Seamless Backend Transition From LevelUp to Paytronix
Discover how Maruti Techlabs ensured a seamless transition for Ann’s Boba Tea from LevelUp to Paytronix,...
-
How I Scaled My Digital Workplace with AI, Automation, and Workforce Apps
40% of managers reported feeling doubtful about their ability to manage remote teams. Asana is a...
-
3 Painfully Obvious Mistakes Early-Stage Founders Keep Making (and How to Dodge Them)
Startups are hard, and I’ve seen (and built) a few that made mistakes so glaring from...
-
Commerce DeFi: How Blockchain Payments Will Fuel the Next Wave of Crypto Adoption
Commerce DeFi bridges decentralized finance (DeFi) with real-world commerce, making crypto practical for daily expenses like...
-
Cybersecurity Is a Scam—And You’re Buying It
Cybersecurity is a multi-billion-dollar industry, yet breaches are more rampant than ever. hacking has become completely...