~hackernoon | Bookmarks (1962)
-
Exit-Problem for a Class of Non-Markov Processes With Path Dependency: State of the Art
Similar systems with path-interaction behaviour have already been studied by numerous researchers for more than 30...
-
Building Generative AI for Everyone: Lessons From Kaustav Das Sharma and Gumloop
Kaustav Das Sharma is the founding engineer at Gumloop, an AI platform. He has designed tools...
-
Meet Spacecoin: HackerNoon Company of the Week
This week, HackerNoon features Spacecoin, the first Decentralized Physical Infrastructure Network (DePIN) project to harness blockchain...
-
Coldware Intensifies Blockchain Adoption Game
Coldware (COLD) is rapidly emerging as a contender for mainstream blockchain adoption, leveraging a scalable and...
-
Open Source Isn't Dead...It's Just Forked
The open source community faces questions about what it means to be truly open. Companies like...
-
DePIN and PayFi: Coldware’s Web3 Community Approach
Coldware’s Web3-native approach is attracting investors who prioritize decentralization and open governance. Coldware is designed to...
-
Coldware Community Jump For Joy
With tokenized finance expected to grow exponentially, Coldware’s real-world applications could make it the go-to financial...
-
The HackerNoon Newsletter: Python: A Deeper Look Into How Django Transactions Work (3/3/2025)
How are you, hacker? 🪐 What’s happening in tech today, March 3, 2025? The HackerNoon Newsletter...
-
Your Brand Is Sinking Without These Three Points of Contact
Brands need to make critical decisions on where they stand and the course ahead.
-
Inside the Math Banks Use to Decide If You’re a Credit Risk
Probability of Default (PD) models are tools used in the banking sector to assess the likelihood...
-
Here's Why Productivity Hacks Don't Work—And What You Should Be Focusing on Instead
Productivity hacks don't work if you don't show up consistently. The secret to getting things done...
-
AutoMapper vs. Mapster—Know When to Use Which With This Guide
AutoMapper and Mapster are two popular libraries for object-to-object mapping in .NET. In this article, we’ll...
-
Claude's Latest Version is EPIC for Programmers
Anthropic has released Claude 3.7 Sonnet, integrating both standard response capabilities and extended reasoning within a...
-
How NASA Engineers Extended the Life of the Hubble Telescope: a Story of Successful Modernizations
Through five shuttle missions from 1993 to 2009, astronauts replaced all major components except the mirrors...
-
Why Your Containers Keep Crashing (And How to Stop the Madness)
Docker containers can crash due to OOM kills, resource exhaustion, or network issues. This guide walks...
-
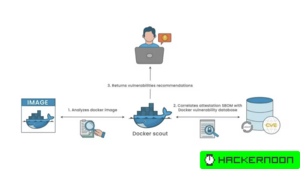
Your Docker Containers Are Probably Full of Security Holes—Here’s How to Fix Them Now
Docker Scout helps prevent container security threats by scanning images for vulnerabilities, generating Software Bill of...
-
AI-Powered Phishing Scams Are Evolving—Here’s How Businesses Can Fight Back
To mitigate sophisticated AI phishing attacks, cybersecurity practitioners and company employees must understand how cyber criminals...
-
How to Steal a Kingdom
In the faltering democratic experiment known as Atlantis, political factions battled for supremacy beneath the swaying...
-
Maybe Trump and Zelenskyy Should Try Blockchain Diplomacy—At Least It Would Keep Them Honest
We need diplomatic relations anchored by the same principles that have made Bitcoin revolutionary: transparency, verification,...
-
U.S. Bets on Blockchain Leadership—The Pacific Islands Should Follow
The recent remarks by Tyler Williams, Counselor to the Secretary of the Treasury, highlight a pivotal...
-
Everything You Need to Know to Spot Scam or Fake Tokens
Scammers often create counterfeit tokens that mimic legitimate assets to deceive investors. Honeypot tokens are built...
-
Lessons From My First Profitable iOS App ($1,400 in 90 Days)
Not a life-changing amount, but enough to prove that small indie apps can make real money....
-
Proactive Issue Detection in Cloud Software
Top tech companies apply a number of sophisticated strategies to detect issues as early as possible....
-
Could the ByBit Hack Have Been Prevented? Yes—Here’s How
The ByBit attack, carried out by the North Korean Lazarus Group, exploited a compromised Safe wallet...