~hackernoon | Bookmarks (1946)
-
Driving Excellence in Scientific Research Support Through ERP Leadership by Chandan Mishra
At a premier U.S. national lab, Chandan Mishra modernized PeopleSoft ERP systems to improve transparency, integrate...
-
Devanand Ramachandran’s Enterprise Playbook: Migrating 7,000 Legacy Apps Without Disruption
With 20+ years of IT expertise, Devanand Ramachandran led the seamless migration of 7,000 legacy Lotus...
-
Write Together, Publish Faster: How to Co-Author Stories on HackerNoon
HackerNoon’s new feature, Chowa, makes collaborative writing easier than ever. Add co-authors, leave inline comments, and...
-
Cutting Private Key Backup Failures by 6 Orders of Magnitude
This paper presents a novel private key backup method using trustee-based indirect-escrow and indirect-permission models, dramatically...
-
How Secure Are Private Key Backup Methods? A Comparative Study
This section compares various private key backup methods, showing that the indirect-permission approach achieves significantly lower...
-
If PCI-DSS Compliance Makes Apps Safer, Why Aren’t We All Doing It?
PCI DSS compliance offers security benefits beyond payments. This guide breaks down practical, dev-friendly secure coding...
-
Set Up a SOCKS Proxy via Azure Blob Storage in Restricted Networks
ProxyBlob lets you tunnel SOCKS5 traffic via Azure Blob Storage, bypassing network restrictions. This guide shows...
-
How to Instantly Delete All Objects and AutoShapes in Excel
Learn two easy ways to delete all objects and AutoShapes in Excel—use the Go To Special...
-
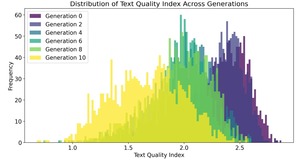
Measuring Text Decay in AI
This article examines how GPT-2's text quality declines with repeated generations, showing increased incoherence and repetition...
-
Optimizing Failure Rates in Trustee-Based Recovery Systems
Real-world data helps optimize trustee-based recovery by choosing (k, n) values that minimize the failure rate,...
-
How Secure Backup Systems Prevent Recovery Failures
Trustee-based encrypted backup systems are secure and reliable when owners use flexible, redundant storage and optimize...
-
How Institutions Are Bridging Crypto and Traditional Banking
The future of finance does not include one system dominating the other. It combines old and...
-
The TechBeat: Decentralized Identity (DID) and KYC in Blockchain Gambling: Privacy vs. Compliance (5/30/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
Acknowledgments: Funding and Support for Explanatory Feedback Research
We acknowledge the funding from the Richard King Mellon Foundation and the Learning Engineering Virtual Institute,...
-
Godot Engine: Introducing the Meta Toolkit Extension
The release of the Godot Meta Toolkit, a GDExtension plugin that exposes Meta’s Platform SDK and...
-
Everything You Need to Know About Rust 1.85.0 and Rust 2024
This stabilizes the 2024 edition as well. Rust is a programming language empowering everyone to build...
-
Go Execution Traces Have Become More Powerful
Go 1.22 and 1.23 are the latest releases of the Go programming language. They include improvements...
-
An Actual Way to Use Reported Crime Data to Prevent Crime
Aaron Sankin: A company called Geolitica developed an algorithm that predicts where and when crimes will...
-
Inside the New Space Race: Firefly, ispace, Axiom, and the Orbital Future
The commercial space sector is hurtling toward a new era marked by lunar returns, private space...
-
Mastering Asynchronous JavaScript Callbacks, Promises, and Async, Await for Cleaner React Components
React is fast. But fast doesn’t always mean efficient—especially when it comes to real-world data.
-
How Island Communities Are Using Blockchain to Escape the Red Button Economy
Island communities are building decentralized infrastructure and adopting Bitcoin to unlock global monetary freedom through DePIN,...
-
Meet Linguado, Antix Interactive, eEPIC Events: HackerNoon Startups of The Week
Each week, the HackerNoon team highlights standout Startups from our Startups of The Year database. Every...
-
The Definition of Tier 1 Media Is Changing (And Lots of Industries Need to Catch Up)
The shift isn’t just SEO vs. social anymore, it’s generative vs. static. People are just as...
-
How to Evaluate Security and Reliability in Key Recovery Systems
Security alone isn't enough. This article presents a joint analysis of security and reliability in key...