~hackernoon | Bookmarks (1960)
-
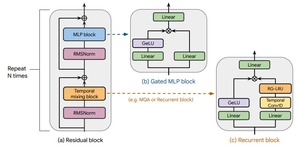
Recurrent Models Scale as Efficiently as Transformers
This research compares MQA Transformers, Hawk, and Griffin models, highlighting Griffin's hybrid approach combining recurrent blocks...
-
The HackerNoon Newsletter: Predicting Crypto 2025: Up, Up, and… Away? (1/13/2025)
How are you, hacker? 🪐 What’s happening in tech today, January 13, 2025? The HackerNoon Newsletter...
-
RG-LRU: A Breakthrough Recurrent Layer Redefining NLP Model Efficiency
This research presents RG-LRU, a novel recurrent layer for temporal mixing, used in Hawk and Griffin...
-
RNN Models Hawk and Griffin: Transforming NLP Efficiency and Scaling
This research introduces Hawk and Griffin, RNN-based models that rival Transformers in efficiency, scaling, and long-sequence...
-
I Over Relied on AI and Those Shortcuts Cost Me
While AI offers efficient shortcuts to problem-solving, it changes the nature of the journey that shapes...
-
New Startups Are Standing Out In a Hyper-competitive Market—Here's How
When your target market is crowded with established players and new entrants, the challenge becomes exponentially...
-
Who Even Needs Undersea Cables for Internet Anymore?
While Starlink has demonstrated the immediate practical benefits of satellite-based internet, emerging technology like Spacecoin is...
-
Insights from VazaZika Developers on Gamified Public Health Software
The study involved a focus group with VazaZika developers, exploring insights on gamified software that promotes...
-
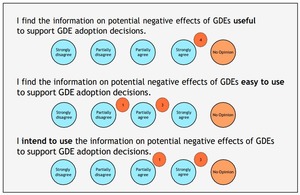
Evaluating the Usefulness of Negative Effects in GDE Adoption
Participants found GDEs’ negative effects useful for adoption, noting context sensitivity and value for developers new...
-
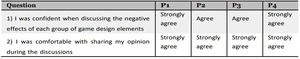
Participant Feedback
Participants felt confident and comfortable discussing GDEs' negative effects, agreeing they could freely share opinions during...
-
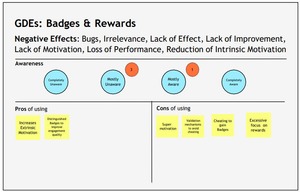
Developers’ Insights on Game Design Elements: Pros and Cons
The focus group explored developers' views on GDEs, identifying pros like motivation and engagement, and cons...
-
This Open-Source Marketing Hack Could Set You Up for Financial Freedom in 2025!
At the beginning of 2024, I started to work on a social media scheduling tool called Postiz....
-
The HackerNoon Newsletter: The Practical Guide to Ethereum Rollups (1/12/2025)
How are you, hacker? 🪐 What’s happening in tech today, January 12, 2025? The HackerNoon Newsletter...
-
Is the Internet Doomed to Fallout? Why Decentralization Is Our Survival Plan
Decentralized Internet envisions a more autonomous, citizen-driven Internet. It redistributes data across numerous nodes, where each...
-
Project DIGITS: NVIDIA’s Leap into Personal AI Supercomputing
Project DIGITS democratizes AI computing by giving developers a powerful desktop untethered from the cloud. DIGITS...
-
Gameboi.AI: Your New 24/7 Airdrop Specialist Is Live on X (Twitter) 🕹️💸
Gameboi.AI is an AI-powered agent transforming Web3 airdrops with interactive, bot-resistant campaigns on X. Earn rewards...
-
Why I Built a SaaS to Replace Myself
Data analysis is among the top jobs to be replaced by AI agents. Change is happening...
-
ERC-7683: Unifying Ethereum With Cross-Chain Intents
ERC-7683 introduces a standard for enabling cross-chain intents on Ethereum, allowing seamless communication between different blockchains....
-
Why a Four-Week Work Cycle is Perfect for Complex Product Releases
Choosing the right release cycle is key. This article recommends a four-week cycle for complex On-Premise...
-
What I’ve Learned (and Broken) Building Zero-Knowledge Applications
ZK Proofs lets you prove something is true without showing why it's true. It's used to...
-
The TechBeat: The Crypto Industry is Overlooking a Critical Factor in Ensuring Its Success (1/12/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
Pretraining Task Analysis On LLM Video Generati
The research analyzes T2V, T2I, and SSL tasks (FP, Painting, AVCont) using 50M video/text-image subsets, with...
-
Experimental Setup For Large Language Model Video Generation
The research examines 2T tokens, fine-tunes for text-to-video tasks, and evaluates zero-shot benchmarks including MSR-VTT, UCF-101,...
-
Task Prompt Design For LLM Video Generation
VideoPoet uses task-specific prefixes with text, visual, and audio tokens, training only on outputs like visual...