~hackernoon | Bookmarks (1983)
-
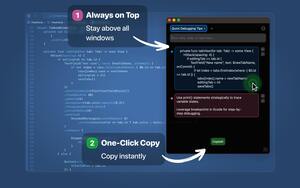
How Building a Jira App Led Me to Create PeekNote — a Minimal macOS Notes Tool for Developers
PeekNote is a lightweight, always-on-top notes app for macOS. Each tab holds a separate text block....
-
This Is What Happens to Telecom Networks When Everyone Streams at Once
A traditional network operation will fail to handle pressure unless it includes adaptive response mechanisms.
-
MindEye2: Novel Functional Alignment for fMRI
It is common for fMRI analyses to align subjects’ brains to a shared space for the...
-
The Secret Financial Struggles Of Healthcare Professionals
Many healthcare workers often face significant financial hurdles before life becomes easier for them. So, if...
-
Here's the Cost of Those AI-Generated Ghibli Images That No One is Talking About
The general public should be sensitized about the consequences of giving away their personal and private...
-
This One Spark SQL Trick Will Instantly Upgrade Your Data Analysis Game
Apache Spark comes with a robust set of window functions, each designed for a different purpose....
-
Working With Web3 Data Is A Lot More Challenging Than One Would Think
In this post, I share my experience working with web3 data. I also summarize the challenges...
-
New Research Discredits the Notion of Crypto as the ‘Slots’ of the Investment World
Investing in crypto is like playing the pokies, i.e. you could ‘win’ or ‘lose’ it all...
-
Forget The Bybit Hack - This is the REAL Crypto Epidemic Fueling Global Crime
Phishing scams are quietly stealing just as much (if not more) crypto than the biggest hacks....
-
INSANE One-click MCP AI Agent Hits the Market
Genspark AI has emerged as a formidable new player in the AI agent space, positioning itself...
-
I Blew €400 on Cursor — Here's What I Learned So You Don't Have To
Building software with Cursor is super fast, and you should definitely use it. However, there are...
-
I Coded Through a Bipolar Manic Episode — Until It Landed Me in the ER
TL;DR: Tech "grindset" is glorified mental illness. Developer discovers manic coding and whiskey isn't sustainable, crashes...
-
So How Scary is The Dark Web Really?
Think the dark web is all crime and hackers? Think again. Let’s bust the myths and...
-
Are Cybersecurity Degrees Worth the Cost?
Is a cybersecurity degree worth the time and money? Explore pros, cons, and alternatives to decide...
-
Hackers Can Teach Us A LOT About Security
Discover how ethical hackers think, why systems get breached, and how you can protect yourself by...
-
Here's How to Convert Time into Decimal Value Using Excel's TIMEVALUE Function
The TIMEVALUE function is useful when your time is in text format and you want to...
-
How Balancer v3’s Launch on Avalanche Could Reshape DeFi Liquidity Infrastructure
Balancer v3 deploys on Avalanche, introducing Boosted Pools and Hooks to optimize DeFi liquidity across one...
-
The 5 Secrets To Getting Featured as Top Story on HackerNoon
Want your story featured on HackerNoon’s homepage? Here are 5 key tips straight from the editorial...
-
Sci-Fi to Sky-Fi: How Pop Culture Inspired Real-World Space Tech
Science fiction has always pushed the boundaries of our imagination. From movies like *Star Wars* to...
-
Proof Of Waste: Why the Blockchain Belongs In The Dumpster
Informal waste disposal is a quiet system that’s thriving—with 20 million people moving junk across the...
-
Analyzing the Impact of Model Scaling on Long-Form Factuality
This section delves into the impact of model scaling on long-form factuality, highlighting the improvement of...
-
The TechBeat: Why Every Front-End Team Needs Storybook (4/11/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
A Kubernetes Special: Even More OpenTelemetry to Chew On
I have presented my OpenTelemetry demo many times, and I still do. Each time, the audience...
-
Educational Byte: What are Real-World Assets (RWA) Tokens in Crypto?
Real-World Assets (RWA) tokens and platforms offer assets that already exist in the real world (the...