Explore
Can You Grok It – Hacking together my own dev tunnel service
My friend sent me a tunnel link where he had to manually set it up with...

House Votes to Extend—and Expand—a Major US Spy Program
The US House of Representatives voted on Friday to extend the Section 702 spy program. It...
Home
Docs Read more details about CIPHERLEAKs. Q&A Who is affected by CIPHERLEAKs?All SEV, SEV-ES and SEV-SNP...

LXer: GStreamer 1.24.2 Brings Security and Bug Fixes
Published at LXer: GStreamer's latest 1.24.2 release fixes security flaws and bugs, including notable fixes in...

The Best Personal Safety Devices, Apps, and Wearables
Your smartphone or wearable could help you out in a truly dangerous situation. Here are some...

DuckDuckGo Is Taking Its Privacy Fight to Data Brokers
Privacy-focused company DuckDuckGo is launching a tool to remove data from people-search websites, a VPN, and...
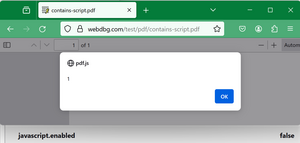
Browser Security Bugs that Aren’t: JavaScript in PDF
A fairly common security bug report is of the form: “I can put JavaScript inside a...

X veränderte User-Beiträge: Gefundenes Fressen für Phisher
Link URL: https://www.heise.de/news/X-veraenderte-User-Beitraege-Gefundenes-Fressen-fuer-Phischer-9681259.html Comments URL: https://tildes.net/~comp/1fjj/twitter_replaces_twitter_com_with_x_com_without_user_consent_bad_implementation_invites_an_influx Votes: 29 Comments: 2

Trump Loyalists Kill Vote on US Wiretap Program
An attempt to reauthorize Section 702, the so-called crown jewel of US spy powers, failed for...
Sama launches AI safety-centered ‘red teaming solution’ for gen AI and LLMs
Sama seeks to leverage AI to address safety concerns around generative AI and large language models...

Notepad++ wants your help in "parasite website" shutdown
The Notepad++ project is seeking the public's help in taking down a copycat website that closely...

How to Protect Yourself (and Your Loved Ones) From AI Scam Calls
AI tools are getting better at cloning people’s voices, and scammers are using these new capabilities...

LXer: In a First, AlmaLinux Patches a Security Hole That Remains Unpatched in Upstream RHEL
Published at LXer: Until last November�s release of AlmaLinux 9.3 you wouldn�t see AlmaLinux issuing a...