Explore

100 Days of AI, Day 17: The Different Ways Security Attacks are Created Using LLMs
This post covers different security attacks possible using LLMs and how developers are adapting to them.
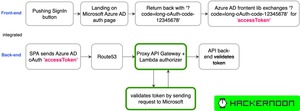
How to Use AWS Lambda Authorizer for Flexible and Scalable Web Service Authorization
On one of the projects I worked on, there were 8 services that used Auth0 for...

So, You Want to Be a Hacker?
This article promotes entry into Capture The Flag (CTF) competitions for beginners interested in cybersecurity and...

Navigating the Future of Blockchain with COTI V2's Privacy Innovations
COTI V2's integration of the Multi-Party Computation (MPC) protocol revolutionizes blockchain privacy by enabling secure, private...

Top 6 Multi-Cloud Security Threats to Be Aware of in 2024
As we head into a new year, having a view of the threats that could potentially...

Kerberoasting Attacks Surge: CrowdStrike's 2023 Warning
Kerberos is a ticket-based authentication system. Kerberoasting is a form of assault on networks secured by...
.css-1q79kkk-skeletonStyles-Skeleton{background-color:#eee;background-image:linear-gradient( 90deg,#eee,#f5f5f5,#eee );background-size:200px 100%;background-repeat:no-repeat;border-radius:4px;displ...
This four-part series sheds light on the often-overlooked factors that shape our digital landscape, highlighting the...

The Zero Knowledge Proofs Writing Contest: Winner Announced!
Here’s the list of the top 10 stories: Zero-Knowledge Proofs: It's Like Magic, but I'll Explain...





